Frequently Asked Questions
General
- What languages are supported in FinalCrypt ?
- How did this software get the name FinalCrypt ?
- Is it legal to protect my privacy with FinalCrypt ?
- Why was the Creative Commons License chosen ?
- How is File Encryption safer than Disk Encryption ?
- Only GPL is OpenSource! Is FinalCrypt OpenSource ?
- Does FinalCrypt gather privacy sensitive information ?
- Is FinalCrypt regularly independently tested for safety ?
- Can other people get involved in the FinalCrypt project ?
- How can we say thank you ? Do you accept donations ?
Technical
- Where do I find FinalCrypt's history and log files ?
- What Operating Systems are supported by FinalCrypt ?
- How do I run FinalCrypt with a custom Java(FX) Install ?
- Where does FinalCrypt create the automatic key files ?
- Can you tell us a bit more about the (Auto) Key Directory ?
- I can't find the Create Key Button anymore! Is it deleted ?
- How secure are FinalCrypt generated cryptographic keys ?
- Can you explain a bit more about how the password works ?
- Can FinalCrypt decrypt across Operating and File Systems ?
- Can FinalCrypt encrypt files in a LUKS / Veracrypt volume ?
- How do I best backup my encrypted files and key files ?
- Why do I see so many strange characters in my .bit files ?
- Why does "myfile.bit" show unencrypted and encryptable ?
- Is there a fast way to find all my key files on my computer ?
- Can FinalCrypt's encryption be command-line automated ?
- Apple MacOS: FinalCrypt.app is damaged ? What can i do ?
- Apple MacOS how do I stop file-manager focus-flashing ?
- FinalCrypt hangs sometimes on Apple MacOS. What can I do ?
- I recovered a securely deleted file! Is it a Security Flaw ?
- Is there a way to compare FinalCrypt logfile checksums ?
- I forgot my password, is there a way to decrypt my files ?
- I lost my key files, is there any way to decrypt my files ?
- Clicking "Logs" doesn't work on Linux! How do I fix this ?
- What is the best way to automate password encrypted files ?
- Does FinalCrypt support raw OTP encryption or Non MAC Mode ?
- Is there perhaps a command-line instruction video available ?
Personal
- Can you tell us a bit about your background ?
General
What languages are supported in FinalCrypt ?
Afrikaans, Amharic, Arabic, Armenian, Azerbaijani, Basque, Belarusian, Bengali, Bulgarian, Burmese, Castilian, Catalan, Chinese, Croatian, Czech, Danish, Dutch, English, Esperanto, Estonian, Farsi, Finnish, Flemish, French, Georgian, German, Greek Modern (1453-), Gujarati, Hebrew, Hindi, Hmong, Hungarian, Icelandic, Igbo, Indonesian, Italian, Japanese, Javanese, Kannada, Kazakh, Korean, Latvian, Macedonian, Malay, Maltese, Marathi, Moldavian, Moldovan, Mong, Mongolian, Nepali, Norwegian, Panjabi, Pashto, Persian, Polish, Portuguese, Punjabi, Pushto, Romanian, Russian, Serbian, Sindhi, Sinhala, Sinhalese, Slovenian, Sotho Southern, Spanish, Swahili, Swedish, Tagalog, Tajik, Tamil, Telugu, Thai, Turkish, Ukrainian, Urdu, Uzbek, Valencian, Vietnamese, Western Frisian, Xhosa, Yoruba, Zulu
Languages can be corrected and added to FinalCrypt. Please read instructions here
How did this software get the name FinalCrypt ?
The software deserved an appropriate name. The most important property is One Time Pad Encryption which can't be broken
Non OTP encryption algorithms will be broken over time. OTP encryption truly is final so therefor it was named FinalCrypt
Is it legal to protect my privacy with FinalCrypt ?
Imagine strangers invading your house, closely observing you and your family members in detail, searching through all your papers and correspondence
In real life this would never be tolerated, but on our computers and cell phones we have no clue. Big Tech knows that you don't know and gets away with it
In most countries privacy is a constitutional right, because it is a very reasonable Human Right by Article 8
Why was the Creative Commons License chosen ?
Because Creative Commons License - Attribution-NonCommercial-NoDerivatives 4.0 International (CC BY-NC-ND 4.0)
legally protects FinalCrypt from people building in back-doors and release a malicious version of FinalCrypt to the public
The more popular GPL3 license does not protect software and users against malicious changes being released to the public
Changing the FinalCrypt source code for personal use is allowed of course
How is File Encryption safer than Disk Encryption ?
With File Encryption when you decrypt one file then all other files remain encrypted
With Disk Encryption when you decrypt one file then all other files on that drive / disk can be accessed unencrypted too.
Only GPL is OpenSource! Is FinalCrypt OpenSource ?
OpenSource: A "Free Software Foundation" fairy tale of Honor and Idealism made up by Capitalists
The term "OpenSource" has been made up by the Free Software Foundation to masquerade their intentions
OpenSource suggests accessible source where in fact legal rights to edit and release derivatives are meant
The meaning "Open" does not mean "Change" as "Open shops" do NOT give you the right to "Change shops"
GPL means that anyone can wait for OpenSource to mature and then run off with it to commercialize / exploit it
GPL licenses seem to be designed in favor of capitalists milking cheap / free "OpenSource" software developers
The common people develop an idealistic need and the industry gets in the middle, scales up for growth and profits
The Free Software Foundation needs to be clear and rename the term OpenSource to reflect on it's intentions like:
"PublicSource", "EditSource", "DerivativeSource", "AllRightsSource", "CommercializeSource", "ExploitSource"
The FinalCrypt sourcecode is available to anyone and even grants edit rights (without commercial / derivative rights)
The danger to edit, commercial & derivative rights
Edit & Derivative rights demands the right to build in anything (like back-doors) and release (counterproductive) derivative works
Allowing building in backdoors is a severe security threat, which is why GPL3 should NEVER be used on security software
Does FinalCrypt gather privacy sensitive information ?
No, that's private, but FinalCrypt's IP address and User Agent String is logged on every Check Update
When FinalCrypt checks for updates it fetches the VERSION2 file just like every Browser would do that
This is how we know how many users there are and what FinalCrypt Version runs on what Operating System
Further than that nothing else is gathered or uploaded
Is FinalCrypt regularly independently tested for safety ?
Yes, all FinalCrypt releases are uploaded to VirusTotal to be scanned for malicious software at 70 anti-virus companies
Please feel free to check FinalCrypt your self for spyware or malware any way you wish or by clicking the checkboxes on the download page
Can other people get involved in the FinalCrypt project ?
Yes absolutely, there are a number of voluntary roles available:
Web Hosters to host and mirror the FinalCrypt website
Translators to translate FinalCrypt to other languages
Ambassadors to promote and create public attention for FinalCrypt
Test Engineers to test FinalCrypt on different systems (where possible)
Security Engineers to find possible exploits and vulnerabilities in FinalCrypt
Support Engineers to support FinalCrypt users on different systems (where possible)
Please contact me if you wish to volunteer: Email | Telegram
How can we say thank you ? Do you accept donations ?
Every “thank you” is really appreciated, but FinalCrypt depends on users spreading the word as I don’t have the financial means to advertise
I don't accept donations, but please thank me by sharing online. FinalCrypt is also a public protest telling “Big Brother” enough is enough!
Technical
Where do I find FinalCrypt's history and log files ?
In your home directory you'll find a subdirectory called: ".finalcrypt\log" (notice the ".")
FinalCrypt 6.3.2 introduced a new "Logs" link at the bottom which directly opens a FileManager
What Operating Systems are supported by FinalCrypt ?
All the major Operating Systems are supported
Microsoft: XP, Vista, 7, 8, 10 etc.
Apple MacOS 10.7.3 or higher
Linux (many distribution)
BSD: FreeBSD, GhostBSD (OpenJFX)
Solaris x64
Solaris Sparc
HPUX (best effort)
AIX (best effort)
The major Mobile Operating Systems are not supported
Apple IOS
Google Android
Windows Mobile
The non major Mobile Operating Systems are best effort supported
Librem PureOS
Plasma Mobile
If anyone has the opportunity and wants to test FinalCrypt on PureOS or Plasma Mobile then you're more than welcome to ask for support
How do I run FinalCrypt with a custom Java Install ?
Quick and dirty (Java 8)
Windows 10 (copy and paste into MSDOS)
curl --output finalcrypt_windows_portable_x64.zip --url https://www.finalcrypt.org/downloads/microsoft/finalcrypt_windows_portable_x64.zip
tar xf finalcrypt_windows_portable_x64.zip
FinalCryptPortable\bin\java -cp FinalCryptPortable\finalcrypt.jar rdj.CLUI
FinalCryptPortable\bin\java -cp FinalCryptPortable\finalcrypt.jar rdj.GUIFX
Linux (copy and paste into terminal)
curl --output "finalcrypt_linux_portable_x64.zip" --url "http://www.finalcrypt.org/downloads/linux/finalcrypt_linux_portable_x64.zip";
unzip finalcrypt_linux_portable_x64.zip;
FinalCryptPortable/bin/java -cp FinalCryptPortable/finalcrypt.jar rdj.CLUI;
FinalCryptPortable/bin/java -cp FinalCryptPortable/finalcrypt.jar rdj.GUIFX;
Apple (copy and paste into terminal)
curl --output finalcrypt_apple_portable_x64.zip --url http://www.finalcrypt.org/downloads/apple/finalcrypt_apple_portable_x64.zip;
unzip finalcrypt_apple_portable_x64.zip;
FinalCryptPortable/bin/java -cp FinalCryptPortable/finalcrypt.jar rdj.CLUI;
FinalCryptPortable/bin/java -cp FinalCryptPortable/finalcrypt.jar rdj.GUIFX;
======================================================================================================================
Download finalcrypt.jar in your home dir
Java 8 (includes JavaFX)
Install (or extract in your home dir) Java 8 follow instructions on page
To run FinalCrypt open DOS Prompt or Terminal and type:
Graphical User Interface (GUI):
java -jar finalcrypt.jar
Command Line Interface (CLI):
java -cp finalcrypt.jar rdj.CLUI
Java 9 or higher
Extract OpenJDK 15 in your home dir
Extract OpenJFX 15 SDK in your home dir
To run FinalCrypt open DOS Prompt or Terminal and type:
Graphical User Interface (GUI):
jdk-15.0.1/bin/java --module-path javafx-sdk-15.0.1/lib --add-modules javafx.controls,javafx.fxml,javafx.swing,javafx.media -jar finalcrypt.jar
Command Line Interface (CLI):
jdk-15.0.1/bin/java --module-path javafx-sdk-15.0.1/lib --add-modules javafx.controls,javafx.fxml,javafx.swing,javafx.media -cp finalcrypt.jar rdj.CLUI
BSD
Install Java(FX):
sudo pkg install `pkg search jfx | awk '{ print $1 }'`
Graphical User Interface (GUI):
java --module-path /usr/local/openjfx14/lib/ --add-modules javafx.controls,javafx.fxml,javafx.swing,javafx.media -jar finalcrypt.jar
Command Line Interface (CLI):
java --module-path /usr/local/openjfx14/lib/ --add-modules javafx.controls,javafx.fxml,javafx.swing,javafx.media -cp finalcrypt.jar rdj.CLUI
Where does FinalCrypt create the automatic key files ??
The short answer is in the Key Directory (selected on the right panel)
Just remember: Key File = [Key Directory] + [Full Path Encrypted File]
Here is an example:
Key Directory : D:\KF\
Encrypted File: C:\Users\steve\Documents\My secret loveletter.doc.bit
Auto Key File: D:\KF\C\Users\steve\Documents\My secret loveletter.doc.bit
If your target files moved to another location and FinalCrypt can't match the keys then there's a trick
Click the Missing Keys number (right panel in FinalCrypt) and FinalCrypt prints the missing key files on the log section.
Search for these key files and restore them to the new matching location. Once restored, FinalCrypt will show them as Matched Keys.
Can you tell us a bit more about the (Auto) Key Directory ?
Your Key Directory holds your One Time Pad Key Files which are automatically created and selected
The first time you use FinalCrypt you can select any empty directory as your (Auto) Key Directory
It's highly recommended that your Key Directory of choice is stored on a fast external USB drive
Every time you start FinalCrypt you go into that same Key Directory (on the external USB drive)
More information on: how Automatic Keys works
It is highly recommended that you also set a password when encrypting in case your key files are lost / stolen.
Backup your encrypted files AND key files together on an external (USB) drive
For more info please see: "How do I best backup my encrypted files and key files ?"
I can't find the Create Key Button anymore! Is it deleted ?
Please don't use the Manual Create Key Mode anymore as Automatic Key Mode has become the standard for some time now
From version 5.6.2 the Create Key Button was removed to prevent confusion on how to use FinalCrypt's Automatic Keys
An invisible link appears when hovering over the "Select One Time Pad Key Dir" Label to create manual keys (if needed)
Here is some history on FinalCrypt Keys:
Initially FinalCrypt started without Key Generator, allowing users to select personal images and videos as key files
The idea was that even supercomputers couldn't guess (render) all combinations until it bit accurately got a picture of me and my cat
Crypto experts then said that FinalCrypt was actually a sort of One Time Pad Encryption breaking OTP rules because of two reasons:
1. Personal images or videos are NOT truly random
2. Re-use of keys (1 key encrypting multi files) causes drastic deduction of random key patterns making encrypted files vulnerable
In version 2.6.0 I added the Create Key button with a cryptographically strong random number generator to comply with One Time Pad security
In version 5.0.0 I added Automatic Key generation, which allowed FinalCrypt to (batch) encrypt all files with One Time Pad security by default
How secure are FinalCrypt generated cryptographic keys ?
On Monday 3 February 2025 FinalCrypt was security audited by ChatGPT AI Security Analyst: HTML / PDF
FinalCrypt uses the Oracle java.security.SecureRandom class as its cryptographic random number generator
Oracle's java.security.SecureRandom is FIPS140-2 & RFC1750 compliant and generates non deterministic output
However, in every external dependency hides a potential uncertainty, which is why extra precautions have been taken
FinalCrypt extra seeds and encrypts two SecureRandom streams with each other to generate even more secure random output
This costs 25% in performance, but the product of these extra precautions add an extra layer of random security to the keys
In 2013 it was confirmed that the NSA inserted a backdoor in the NIST certified cryptographically secure pseudorandom number generator
Breaking encryption is the NSA's core business, therefor (as a cryptographic software developer) you can never be too cautious!
See visual cryptographic key quality analysis between FinalCrypt and GPG
Can you explain a bit more about how the password works ?
Using a password is optional, but highly recommended in case your key-files are lost or stolen
The optional password effectively encrypts your files twice (multi key encryption) in addition to OTP key encryption
When someone finds your encrypted files (encrypted without password), together with your key files then they could simply decrypt them
When you encrypt your files with an optional password then your encrypted files still can't be decrypted with only your lost / stolen key-files
Can FinalCrypt decrypt across Operating and File Systems ?
Yes FinalCrypt can decrypt across different Operating Systems and File Systems
However, UNIX systems (such as Apple MacOS and Linux) mount file-systems at different locations
which causes the directory structure of encrypted files to change, going from one system to another
FinalCrypt then can't find the keys anymore as it expects encrypted file paths to be identical to the key file paths underneeth the Key Directory
Example 1 - Windows Encrypted Documents with USB Flash Drive with FinalCrypt Key Dir:
Operating System |
Encrypted File |
Key Directory |
Key File |
MS Windows initial key path |
C:\Users\user\Documents\mydoc.doc.bit |
D:\ |
D:\C\Users\user\Documents\mydoc.doc.bit |
-Apple MacOS -faulty key path |
/Users/user name/Documents/mydoc.doc.bit |
/Volumes/Keys/ |
/Volumes/Keys/D/Users/user/Documents/mydoc.doc.bit |
-Apple MacOS correct key path |
/Users/user name/Documents/mydoc.doc.bit |
/Volumes/Keys/ |
/Volumes/Keys/D/Users/user name/Documents//mydoc.doc.bit |
Example 2 - Windows Encrypted Files on USB Flash Drive with FinalCrypt Key Dir on USB Flash Drive:
Operating System |
Encrypted File |
Key Directory |
Key File |
MS Windows initial key path |
D:\mydoc.doc.bit |
E:\ |
E:\D\mydoc.doc.bit |
-GNU/Linux -faulty key path |
/media/user/Docs/mydoc.doc.bit |
/media/user/Keys/ |
/media/user/Keys/D/mydoc.doc.bit |
-GNU/Linux correct key path |
/media/user/Docs/mydoc.doc.bit |
/media/user/Keys/ |
/media/user/Keys/media/user/Docs/mydoc.doc.bit |
Correcting the key directory structure (from
red to
green) puts the Key Files where FinalCrypt expects them
The only thing you need to keep in mind is:
Key File = [Key Directory] + [Encrypted File Full Path]”
Correct the key directories while you check the
Key Match field to see if the key files match up again
If you're having difficulty realigning the key directory structure then there's a little trick you can do to make it a bit easier:
Copy an
unencrypted file (with a File Manager) to your (root)
Target Directory (left side)
and select it as a target and select your Key Directory (right side)
Click on the
Create Keys number showing [1]. to
print the path of the key that would be created for this file.
That path is where your Key Directory is expected
In Juli 2019 FinalCrypt was Cross OS & FS tested with FAT32 & ZFS data-files and NTFS, EXT4 & ZFS key-files
First encrypted on Windows 10 and then decrypting on Linux (Ubuntu 18.04) and FreeBSD 13 / GhostBSD 19.04
Can FinalCrypt encrypt files in a LUKS / Veracrypt volume ?
Yes FinalCrypt (like most applications) has no notion of any underlying disk encryption
FinalCrypt just creates files and writes file-data to any physical or logical file-system
This has been tested on LUKS and VeraCrypt successfully (with different file-systems)
How do I best backup my encrypted files and key files ?
Make sure that at every backup you also backup your key files together with your encrypted files as pairs
Decrypting your files also deletes the correlating key files. When re-encrypting then new keys are created
It is for this reason that re-encrypted files can not be decrypted with previous versions of key files
Backups of encrypted file - key pairs can be quite simple
Just schedule 1 backup that has 2 includes:
Include 1: My Documents (holding your encrypted files)
Include 2: Key Directory (holding your (My Documents) key files)
The backup output (on USB drive) will usually be a directory name with a (backup) date
Every time you backup, a new backup directory with a new date will be added.
Good backup solutions make sure that unchanged files (between the last backup and the current backup) are hard linked before it synchronizes the changes
That way backups only grows when files change, but it only works on file systems that support hard links like NTFS for Windows 10 and all other UNIX file systems
Linux has Back in Time & Apple has Time Machine for hard linked backups, so you only need to find equivalents for Windows
Why do I see so many strange characters in my .bit files ?
Most likely you're using a texteditor like notepad or wordpad to open up a .bit file
Encrypted file data is virtually all random binary data comming from random key data
Text editors don't know what text encoding to use on random data and use default encoding
Modern computers use UTF8 encoding (large variety of international characters and symbols)
Why does "myfile.bit" show unencrypted and encryptable ?
Those are probably keys not having a Message Authentication Code (MAC)
FinalCrypt does not recognise encrypted files by the .bit extension
FinalCrypt looks inside the file to see if it has a Message Authentication Code (MAC)
The MAC consists of 2 x 70 bytes located at the beginning of the data. You can use a hex-editor to see the MAC
The 1st 70 bytes is fixed plain text: "FinalCrypt - One Time Pad File Encryption - Plain Text MAC Version 003"
The 2nd 70 bytes is the encrypted version of the plain text. This is how FinalCrypt authenticates encrypted files
Is there a fast way to find all my key files on my computer ?
Your (Auto Key) key files have identical names of their encrypted files and also have a .bit extension
Doing a search for .bit files would also match all your encrypted files, so how can you tell them apart
FinalCrypt also can't tell if a file is a Key File, without having the encrypted file and the password
But there's a trick that might help by doing the following: (FinalCrypt does not traverse Linked directories)
Download JAVA 8 to the “Downloads“ directory
Download finalcrypt.jar to your “Downloads“ directory.
Open a Files-Manager and go to your “Downloads” directory and Install JAVA 8
Start a DOS Shell: (Windows) Open StartMenu and search for "cmd" and open it and type:.
================================================================================
java -cp Downloads\finalcrypt.jar rdj.CLUI --decrypt --test -w "*.bit" -k . -t Documents\
Scanning files...finished
No decryptable targets found
Wrong key / password?
Scanning results:
C. Continue test
1. print 51 decrypted files (409,5 MiB)
2. print 51 encryptable files (409,5 MiB)
3. print >.6.3.2 encrypted files (94,0 GiB)
4. print 0 decryptable files (0,0 Bytes)
5. print 0 empty files
6. print 0 symlink files
7. print 0 unreadable files (0,0 Bytes)
8. print 0 unwritable files (0,0 Bytes)
9. print 99 hidden files (12,8 MiB)
10. print 0 unencryptable (0,0 Bytes)
11. print >.6.3.2 undecryptable (94,0 GiB)
12. print 0 key matched files (0,0 Bytes)
13. print 51 key write files (409,5 MiB)
What list would you like to see ? 1
================================================================================
Now print num 1 the decrypted files
Can FinalCrypt's encryption be command-line automated ?
Yes, FinalCrypt has a fully featured command-line interface.
FinalCrypt's command-line interface has even more flexible and powerful features
The command-line interface is called rdj.CLUI and requires you to prepare the following:
Download JAVA 8 to the “Home“ directory.
Download finalcrypt.jar to your “Home“ directory.
Open a Files-Manager and go to your “Home” directory.
Install JAVA 8 and open a DOS Prompt "cmd" / shell (UNIX) and type:
java -cp finalcrypt.jar rdj.CLUI
Press [Enter] to read the manual page.
The FinalCrypt graphical user-interface can help you to quickly learn how to use the command-line interface.
As soon as the GUI is ready to en/decrypt a Print Command button appears in the lower right corner.
Clicking the Print Command button shows an example of what a command-line equivalent command looks like.
Click here to read FinalCrypt's command-line manual page
Apple MacOS: FinalCrypt.app is damaged ? What can I do ?
Mainly there are two reasons why this happens:
1. MacOS 11 (Big Sur)
Invalid certificate. FinalCrypt is not Apple Identified (paying for Apple certificates). Try the Portable Package. Instructions are here and here and a video
Security &Privacy Setting. Can be fixed if you can: -> set Allow software from 3rd parties. Please follow below instructions
2. MacOS 10 (Catalina and lower)
Security &Privacy Setting. Can be fixed if you can: -> set Allow software from 3rd parties. Please follow below instructions
Open "System Preferences"
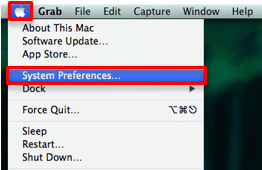
Select "Security & Privacy"
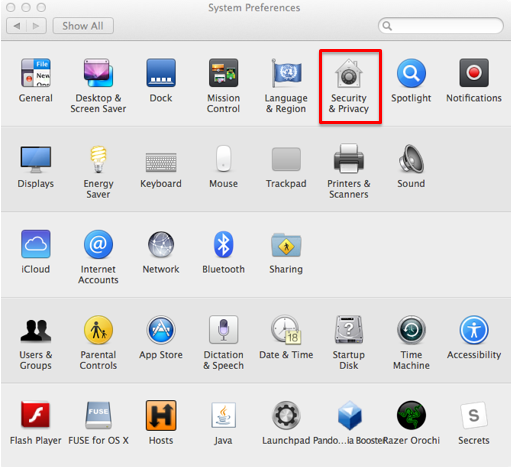
Select the "General" tab and click the lock (lower left)
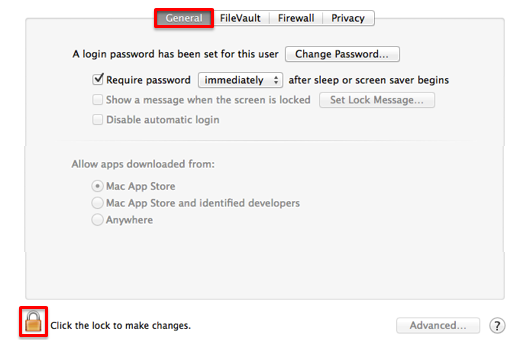
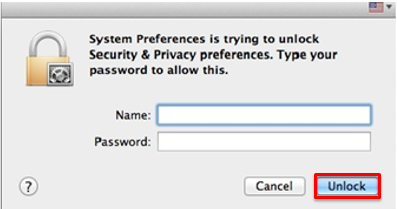
Enter your computer username and password, then select "Unlock."
In the "Allow apps downloaded from:" section, select the radio button to the left of "Anywhere."
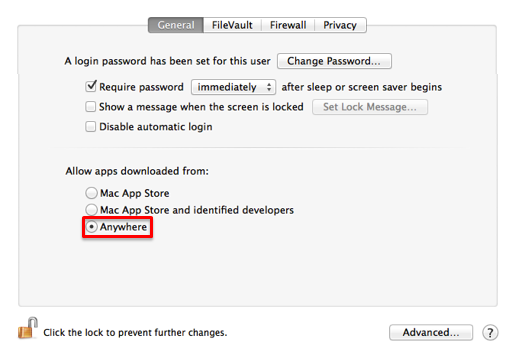
Try again starting FinalCrypt
On Apple MacOS how do I stop file-manager focus-flashing ?
FinalCrypt 5.6.6 solved the Apple MacOS file-manager focus-flashing problem, please update to the latest version and let me know if it happens again
If flashing happens on Apple MacOS it can be stopped by clicking the Log Tab followed by clicking the Encrypt Tab again in the upper left corner
FinalCrypt hangs sometimes on Apple MacOS. What can I do ?
FinalCrypt 5.6.6 solved the Apple MacOS hang problem, please update to the latest version and let me know if it happens again
The previous FinalCrypt GUI could hang sometimes on Apple MacOS after encrypting / decrypting, but usually after finishing en/decryption
The FinalCrypt log files "/Users/$USER/.finalcrypt/log/" allow you to check whether FinalCrypt properly finished en/decryption
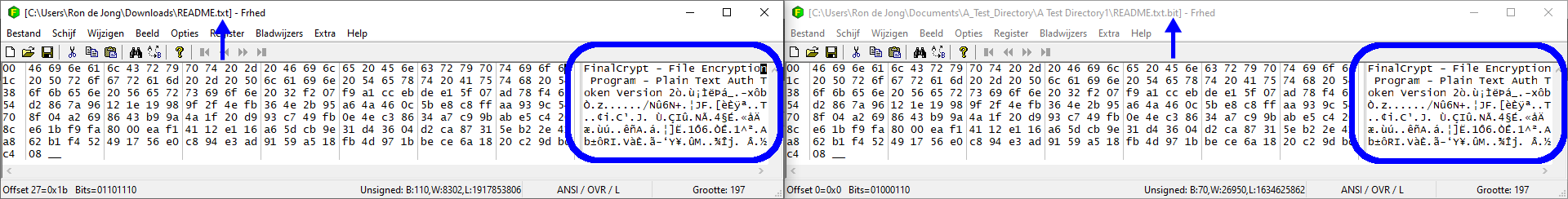
I recovered a securely deleted file! Is it a Security Flaw ?
No, it's not a security bug or flaw. You might be able to recover deleted files with file recovery tools like Recuva
but before FinalCrypt deletes the original file it writes the encrypted data to the original file (similar to Shredding). Reading the old (un)deleted files with a Hex Editor
you'd only see a copy of the new file's content to keep data consistency between the old and new file after en/decoding
Here is an example of an original securely deleted, but recovered file (on the left) and its encrypted counterpart on the right having identical data
Is there a way to compare FinalCrypt logfile checksums ?
Yes, but only for UNIX/Linux as a shell script called: finalcrypt_compare_logs.bash
The way it works is as follows:
You start FinalCrypt and encrypt a set of files and after finishing close FinalCrypt
You again start FinalCrypt and decrypt the same set of files and close FinalCrypt
You can do that in the encrypt - decrypt order or in the decrypt - encrypt order
Then after a full cycle of back and forth encryption you can use the script
You can find the FinalCrypt logfiles in your homedir here: "~/.finalcrypt/log/"
The script checks the function performed in the logfiles you parse on the command line
The log filenames below are just examples, you can use the original log filenames
Usage:
./finalcrypt_compare_logs.bash [-v] encrypt.log decrypt.log
or
./finalcrypt_compare_logs.bash [-v] decrypt.log encrypt.log
It can even cross compare all function combinations like:
./finalcrypt_compare_logs.bash [-v] decrypt.log decrypt.log
./finalcrypt_compare_logs.bash [-v] decrypt.log encrypt.log
./finalcrypt_compare_logs.bash [-v] encrypt.log decrypt.log
./finalcrypt_compare_logs.bash [-v] encrypt.log encrypt.log
The script knows which checksums should be identical and print differences
That's how I do massive 100% integrity tests on 90 GiB of test data / files
I forgot my password, is there a way to decrypt my files ?
Maybe you could try the new FinalCrypt v5.6.0 Brute Force Password Dictionary Scan function
It only works from the command line interface, which requires you to prepare the following:
Download a password dictionary file to the Downloads directory
Download JAVA 8 to the “Downloads“ directory.
Download finalcrypt.jar to your “Downloads“ directory.
Open a Files-Manager and go to your “Downloads” directory.
Install JAVA 8 and extract the Password Dictionary (rename it dictionary.txt)
Open a DOS Prompt "cmd" / shell (UNIX) and type:
java -cp Downloads\finalcrypt.jar rdj.CLUI --scan --password-dictionary "Downloads\dictionary.txt" -k "mykeydir" -t "myfile"
Best is to pick one target file to Brute Force and of course correct "mykeydir" and "myfile" in the above example
FinalCrypt prints 1 second interval progress trying all passwords and stops when it finds your lost / forgotten password
Beware that brute-forcing passwords comes without guarantees. It all depends on how hard your password is to guess
I lost my key files, is there any way to decrypt my files ?
No, sorry, this is why you need to make backups!
Clicking "Logs" doesn't work on Linux! How do I fix this ?
This is a known issue with Ubuntu based Linux distributions
The default file manager nautilus reports a similar error:
(nautilus-autorun-software): WARNING : Unable to find device for URI: Containing mount for file /home/user/.finalcrypt/log not found
To fix the issue open a terminal and type:
xdg-mime default nautilus.desktop inode/directory application/x-gnome-saved-search
Now try clicking "Logs" again in the GUI
What is the best way to automate password encrypted files ?
A very interesting question and one that does deserve the utmost care for security reasons
There are 3 ways to pass a password to finalcrypt's command line interface:
Method 1: Password Parameter
java -cp finalcrypt.jar rdj.CLUI --encrypt -p "mypassword" -k "D:\My\FinalCrypt\KeyDir\" -t "C:\Users\betty\Documents\MyEncryptedFiles\"
The password parameter is a password string parsed on the command line, non-interactive, easy, but not very safe because the password (parameter) can become visible in a process list
Method 2: Password Prompt
java -cp finalcrypt.jar rdj.CLUI --encrypt -pp -k "D:\My\FinalCrypt\KeyDir\" -t "C:\Users\betty\Documents\MyEncryptedFiles\"
Password: ********
The password prompt is much more safe but the user is interactive prompted, so harder to automate when typed live from the keyboard
Method 3: Password Input Redirection
stty -echo
printf "Password: "
read password
stty echo
printf "\n"
echo "${password}" | java -cp finalcrypt.jar rdj.CLUI --encrypt -pp -k "D:\My\FinalCrypt\KeyDir\" -t "C:\Users\betty\Documents\MyEncryptedFiles\"
This is the best and most secure way to automate passwords. A wrapper script that prompts you for a password and can repeatedly and invisibly forward it to FinalCrypt via an input redirected password prompt
Does FinalCrypt support raw OTP encryption or Non MAC Mode ?
Yes it is still supported from the command line interface, but it was removed from the GUI
It caused too much confusion in the GUI so it was removed to prevent double encryption
Non MAC Mode can't tell if a file is decrypted, encrypted or decryptable without a Message Authentication Code (MAC)
Your original unencrypted files will be XORed (encoded) with automatically created key-files and an optional password
The added bit extension suggests that the data file is encrypted and an existing corresponding key will XOR / reverse
That existing re-encrypting / reversing key will not be removed, but overwritten at reencrypting the original again
This is done on purpose so that when you supplied a wrong password, you can still reverse using the old key manually
When the original file has no bit extension a corresponding key is forcefully created / overwriting any existing key
So bare in mind that using Non MAC Mode / raw OTP encryption the gryptographer is required to do the integrity checking
The cryptographer should always verify that decryption succeeded, optionally by using FinalCrypt SHA-256 checksum logging
Use the "--disable-MAC" option as follows in this (Linux) command line test-archive example:
From version 6.8.0:
Encrypt
java -cp finalcrypt.jar rdj/CLUI --encrypt --disable-MAC -k a_test_dir/key_dir/ -t a_test_dir/test_dir1/Manuals/
Decrypt (by encrypting again)
java -cp finalcrypt.jar rdj/CLUI --encrypt --disable-MAC -k a_test_dir/key_dir/ -t a_test_dir/test_dir1/Manuals/
Before version 6.8.0
Encrypt
java -cp finalcrypt.jar rdj/CLUI --encrypt --disable-MAC -k a_test_dir/key_dir/ -t a_test_dir/test_dir1/Manuals/
Decrypt (by encrypting again) no support for: key & target directories
java -cp finalcrypt.jar rdj/CLUI --encrypt --disable-MAC -k "a_test_dir/key_dir/home/ron/a_test_dir/test_dir1/Manuals/Nefit Proline HRC 30.pdf.bit" -t "a_test_dir/test_dir1/Manuals/Nefit Proline HRC 30.pdf.bit"
A "--print" option for education purposes is availabble to see exactly what is happening (manual key & target file mode example)
Creating Data & Key file
echo -n -e \\x05 > myfile # 00000101
echo -n -e \\x03 > mykey # 00000011
Encrypt
java -cp finalcrypt.jar rdj/CLUI --encrypt --print --disable-MAC -k mykey -t myfile
|--------|-------------------|
| | bin hx dec c |
|--------|-------------------|
| Input | 00000101 05 005 ? |
| Key | 00000011 03 003 ? |
| Output | 00000110 06 006 ? |
|--------|-------------------|
Decrypt (by encrypting again)
java -cp finalcrypt.jar rdj/CLUI --encrypt --print --disable-MAC -k mykey -t myfile.bit
|--------|-------------------|
| | bin hx dec c |
|--------|-------------------|
| Input | 00000110 06 006 ? |
| Key | 00000011 03 003 ? |
| Output | 00000101 05 005 ? |
|--------|-------------------|
Is there perhaps a command-line instruction video available ?
Yes here it is
Personal
Can you tell us a bit about your background ?
Sure, please see my About page

 Number 1
Number 1 Number 2
Number 2 Number 3
Number 3 Number 4
Number 4 Number 5
Number 5 Number 6
Number 6 Number 7
Number 7 Number 8
Number 8 Number 9
Number 9 Number 10
Number 10 Number 11
Number 11 Number 12
Number 12 Number 13
Number 13 Number 14
Number 14 Number 15
Number 15 Number 16
Number 16 Number 17
Number 17 Number 18
Number 18 Number 19
Number 19 Number 20
Number 20






